In today’s digital landscape, protecting sensitive information and mitigating cybersecurity threats is crucial for organizations of all sizes. Information security incident management plays a vital role in identifying, responding to, and recovering from security incidents. In this comprehensive guide, Newsmartz will explore the key aspects of information security incident management, including its definition, importance, incident response phases, best practices, and proactive measures organizations can take to strengthen their security posture.
Information Security Incident Management: A Comprehensive Guide
Information security incident management is a critical component of an organization’s cybersecurity strategy. By adopting a proactive and systematic approach to incident detection, response, and recovery, organizations can effectively safeguard their information assets, maintain business continuity, and protect their reputation. Implementing best practices, fostering collaboration, and continuously improving incident response capabilities are essential for staying resilient in the face of evolving cybersecurity threats. With a comprehensive understanding of information security incident management, organizations can enhance their security posture and better protect themselves from potential security breaches.
- Understanding Information Security Incident Management:
Information security incident management refers to the process of handling and responding to security incidents within an organization. A security incident is any event or occurrence that poses a potential or actual threat to the confidentiality, integrity, or availability of information systems and data. Incident management involves a systematic approach to detect, analyze, contain, eradicate, and recover from security incidents while minimizing their impact on business operations. - The Importance of Information Security Incident Management:
Effective information security incident management is essential for several reasons. It enables organizations to promptly detect and respond to security incidents, minimizing the potential damage and impact on sensitive data and systems. Incident management also helps organizations comply with legal and regulatory requirements, safeguard their reputation, maintain customer trust, and mitigate financial losses associated with security breaches. - Incident Response Phases:
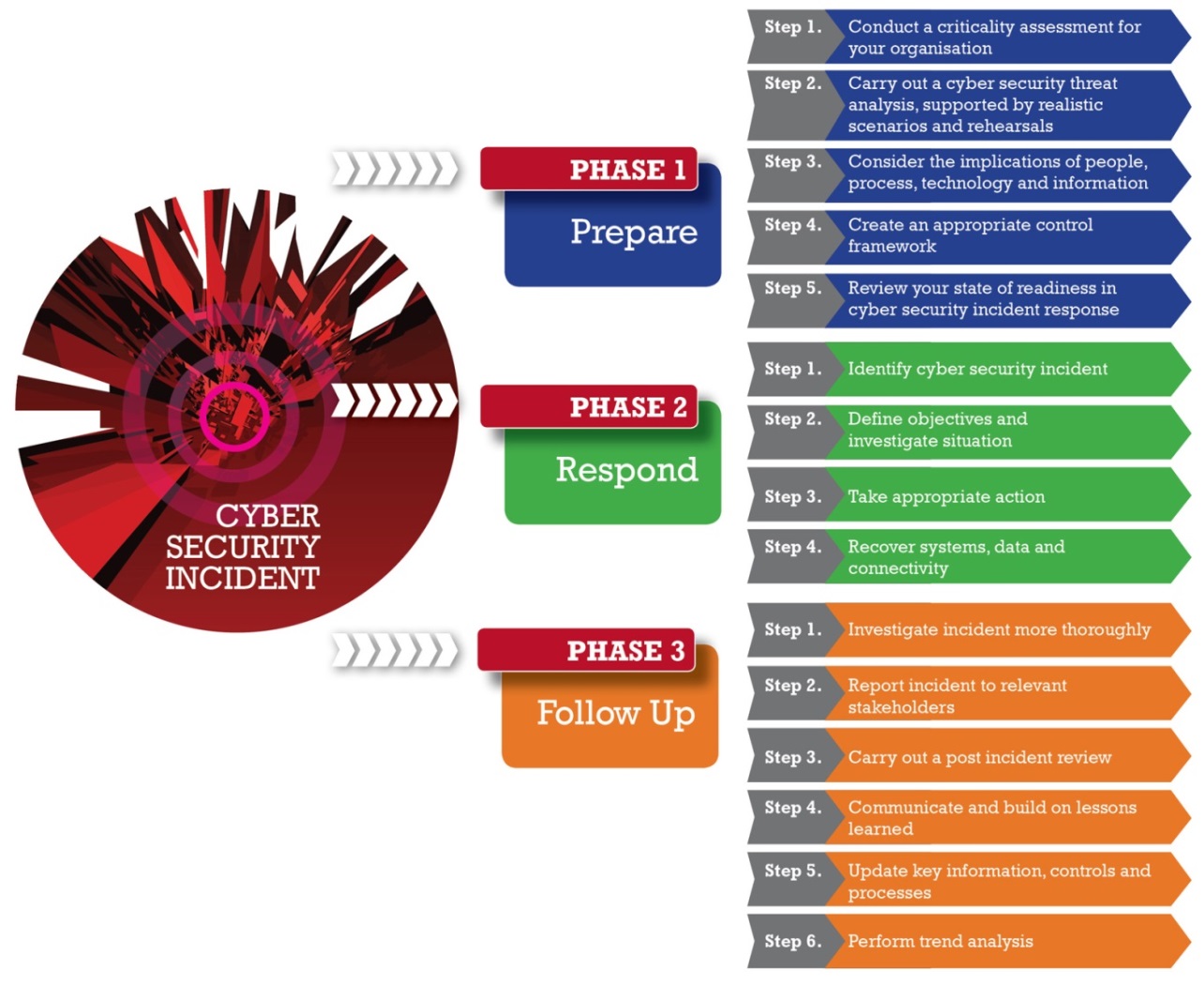
Information security incident management follows a structured framework consisting of several phases. These phases include preparation, detection and analysis, containment, eradication and recovery, and post-incident analysis. Each phase has specific objectives and activities that contribute to a comprehensive incident response process. By understanding these phases, organizations can effectively manage security incidents and minimize their impact. - Best Practices for Information Security Incident Management:
Implementing best practices enhances the effectiveness of information security incident management. Some key best practices include developing an incident response plan, establishing an incident response team, conducting regular training and awareness programs, leveraging incident response tools and technologies, establishing communication and coordination channels, and conducting post-incident analysis to improve incident response capabilities continually. - Proactive Measures for Strengthening Security:
In addition to incident response, organizations should adopt proactive measures to strengthen their overall security posture. These measures include implementing robust security controls, conducting regular risk assessments and vulnerability scans, maintaining up-to-date security policies and procedures, implementing employee security awareness programs, and staying informed about emerging threats and industry best practices. Proactive measures help organizations identify and address potential vulnerabilities before they are exploited.
- Collaboration and Communication:
Effective information security incident management requires collaboration and communication among various stakeholders. Organizations should establish clear lines of communication and define roles and responsibilities for incident response team members, IT personnel, management, legal counsel, and public relations. Regular communication ensures a coordinated and efficient response to security incidents, minimizes confusion, and facilitates the sharing of critical information. - Incident Reporting and Documentation:
Accurate incident reporting and documentation are crucial for effective incident management. Organizations should establish a standardized incident reporting process to capture essential details, such as incident type, date and time, impact assessment, actions taken, and lessons learned. Proper documentation helps organizations analyze trends, identify recurring issues, and improve incident response procedures over time. - Continuous Monitoring and Improvement:
Information security incident management is an ongoing process that requires continuous monitoring and improvement. Organizations should regularly assess their incident response capabilities, conduct tabletop exercises and simulations, update incident response plans, and stay informed about emerging threats and industry trends. By embracing a culture of continuous improvement, organizations can adapt to evolving security landscapes and enhance their incident management capabilities. - Compliance and Legal Considerations:
Information security incident management must align with legal and regulatory requirements specific to the organization’s industry and jurisdiction. Organizations should consider factors such as data breach notification laws, data protection regulations, and industry-specific compliance standards. Compliance with these requirements helps organizations avoid legal consequences and demonstrates a commitment to safeguarding sensitive information.
- Conclusion:
Information security incident management is a critical component of an organization’s cybersecurity strategy. By adopting a proactive and systematic approach to incident detection, response, and recovery, organizations can effectively safeguard their information assets, maintain business continuity, and protect their reputation. Implementing best practices, fostering collaboration, and continuously improving incident response capabilities are essential for staying resilient in the face of evolving cybersecurity threats. With a comprehensive understanding of information security incident management, organizations can enhance their security posture and better protect themselves from potential security breaches.